
Using Snapshots to Improve Data Security
How snapshots — point-in-time copies of data — can improve data security.
You're on page 4, See the latest articles on Cloud Security.

How snapshots — point-in-time copies of data — can improve data security.

The Scarleteel threat targets AWS Fargate environments for data theft and more malicious types of attacks such as cryptojacking and DDoS. Learn how to mitigate this threat.

The White House has announced the first iteration of the National Cybersecurity Implementation Plan. Read on to learn more about the plan and alignment with the five essential pillars.

There are a lot of considerations when adopting a multicloud infrastructure. Use our guide to compare the top 7 multicloud security solutions.

Which VPN works best on iPhones? Use our guide to compare the pricing and features of the 6 best VPNs for iPhone.

Read about penetration testing in cloud security and its importance, details about how it's done and the most common threats to cloud security.
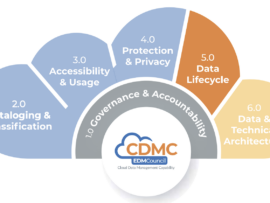
The Council’s first benchmark found that 84% of companies have not implemented ethical access, use and outcome policies and procedures per their cloud agendas.

Thales cloud security study shows that 79% of organizations have more than one cloud provider and 75% of companies said they store at least 40% of their sensitive data in the cloud.

Global survey shows why you fear what you can't see: Confidence in security posture soars but so do worries about unseen vulnerabilities.

Generative AI will be a game changer in cloud security, especially in common pain points like preventing threats, reducing toil from repetitive tasks, and bridging the cybersecurity talent gap.

Zero-trust security has become a hot topic in cybersecurity.. But confusion remains about what it is and how to make it a reality in the enterprise. Here are five tips on implementing zero trust.

New research on operational technology vulnerabilities by Armis found that 56% of engineering workstations have at least one unpatched critical severity.

Syxsense now offers more IT and endpoint management functions, including mobile device management, automation, remediation and zero trust.

The FIDO Alliance’s Andrew Shikiar explains how passkeys are quickly replacing passwords as the next-generation login, a low friction, high security protocol for any device.

Looking for the best VPNs for Chrome extension to enhance your online security and privacy? Dive into our list of top rated VPNs and find your best fit.